


When it comes to ERP security controls, experience matters.
Vulnerabilities exist in all enterprise resource planning (ERP) systems because out of the box, these systems don't come with the controls enabled that regulators, management and internal auditors demand.
It takes years of experience to identify and design optimal ERP controls, develop efficient ways to test them and remediate ERP control failures. Staying on the "cutting edge" of ERP security controls is difficult. Rather than continually training your staff and using their time to perform ERP risk assessments, it makes sense to partner with experienced professionals who do this work every day. That gives your employees the freedom to work on higher-value projects.
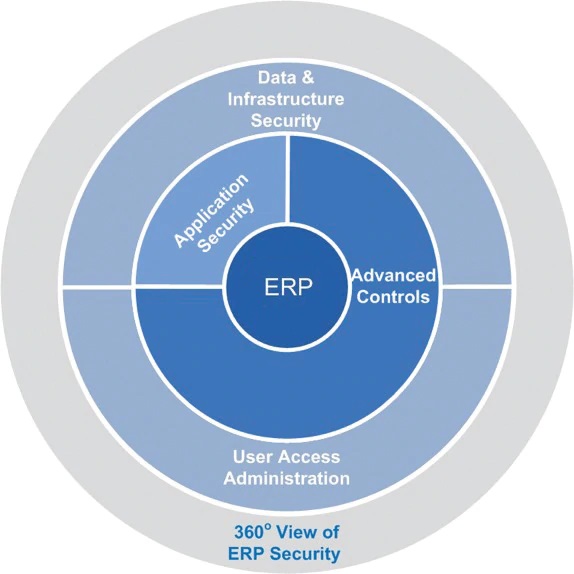
What should the conditions be for a disgruntled employee to commit a specific type of fraud in the system?
* A user still valid in the system (active, unlocked)
* The user should have specific authorizations to execute a program in production
* The user should know he/she has the specific authorizations to commit fraud
* The user should find a way to avoid being detected. Most likely running several very small financial operations.
If the controls above are properly in place, it is very hard to comply with all these conditions at the same time. Even if one of these controls fails, there are other controls that still work. It is very unlikely that all these controls fail in this scenario.
Certain critical vulnerabilities (such as the known misconfigurations targeted by the public 10KBLAZE exploit) allow anyone to bypass authentication (access without user credentials), authorizations (execution without privileges), and change logs (changes without traces).
Now, what should the conditions be for a disgruntled employee to execute the same type of fraud in the system if one single critical
vulnerability is there?
* A user needs access to Google to download an exploit
* The user needs access to Google to understand SAP master tables
* The user needs to follow the steps explained in the exploit documentation
Even if all the controls mentioned above are working properly. The fraud can still be executed. These critical vulnerabilities allow bypassing all the "traditional" IT General Controls as they focus mostly on preventing bad actions from happening in the "traditional" way. If any kind of malicious action is executed in a different way, then those controls can be bypassed.
After reading this, some people may say "well... What is the likelihood of something like that actually happening?"
In 2016 and 2018, the U.S. Department of Homeland Security released two different US-CERT alerts about malicious cyber activity targeting ERP systems. In May 2019, the public release of 10KBLAZE exploits made the DHS publish another US-CERT alert to make organizations aware of this new threat targeting existing SAP misconfigurations. While these misconfigurations were previously known, the impact of a potential attack was always high, but the release of the public exploits significantly increased the likelihood of an attack.
Last but not least, IDC just published a survey of 430 IT decision-makers that found 64% of respondents reported that their ERP systems have been breached in the last 24 months.
After reading this, you may wonder where and how to start an internal cross-departmental conversation with executives. Here you have some key
questions you can ask that will trigger new discussions:
* How has the scope of IT General Controls (ITGC) been defined for each business-critical application?
* Are cybersecurity controls part of the scope defined by ITGC? For example: vulnerability management, log configuration, and management,
configuration baselines, network interfaces between systems, etc.
* Has continuous monitoring of threats (both internal and external) in the business-critical application been properly established?
* What tools have been implemented to monitor specific financial reporting systems?
* How often are critical security patches for your business-critical applications reviewed and implemented?
* What cybersecurity controls have been established for customized code used in business-critical applications for financial reporting?
* How are key cybersecurity controls being mapped to other regulations (besides SOX), such as NERC-CIP, PCI, GDPR, etc?
* How can the external auditor, internal auditor and management assess and test these controls above to provide the right level of assurance?
If you are interested in running a free assessment of your SAP or Oracle EBS systems to determine the level of exposure to serious deficiencies,get
in touch with our senior partners.Adan's consultants have extensive knowledge of ERP systems, including:
* SAP
* Oracle
* PeopleSoft
* JDE
* Microsoft Dynamics
* NetSuite
* Epicor, and more
Our professionals can also help you with governance, risk and compliance (GRC) tools, including GRC tool selection, rule-set implementations, assessments, and designing GRC programs that maximize your GRC tool investment. When it comes to ERP security controls, one size does not fit all. Our ERP risk advisory team uses Adan Corporate's proven ERP methodology and automated assessment tools, based on industry-leading practices, and customizes our services to meet your needs.
Whether you need help designing controls during an ERP implementation, performing an ERP security assessment, establishing ongoing ERP controls monitoring or anything in between, Adan Corporate can help.
Adan Corporate's consulting services for ERP systems include:
* ERP controls risk services
* ERP security controls monitoring
* ERP implementation risk services
You've made a significant investment in your ERP system. When it comes to risk prevention, turn to an advisor you can trust - someone who understands compliance, your ERP system and your needs.

